Kerberos authentication for K2 Smartforms
- What is Kerberos
Kerberos authentication is a security protocol that allows delegation of users’ credentials across multiple servers, allowing a server to impersonate the user to another server or service. In contrast, NTLM the default enabled IIS security protocol, does not support delegation of identity across servers.
K2 Automated Testing Software
BenchQA allows full test automation of K2, including fully automated K2 SmartForms and K2 Workflow testing. It promotes test driven development for K2 and ensures continued quality assurance for K2 solutions. Easily apply changes to test cases to accommodate changes to K2 apps and ensure all apps are regression tested to avoid defects and assure continuous quality.
https://msdn.microsoft.com/en-us/library/windows/desktop/aa378747(v=vs.85).aspx
- When do we need Kerberos for K2 applications
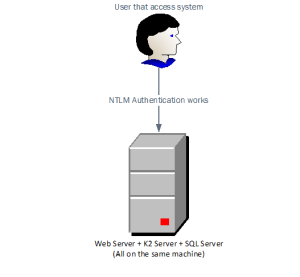
In a previous blog post (http://blog.velocity-it.com/2015/05/18/sql-user-impersonation-with-k2/) we discussed how to setup the K2 server to impersonate a user in SQL server. This allows us to prevent a user from accessing data to which the user doesn’t have the rightful permissions to. In most small-scale K2 environments the web server (IIS), application server (K2 blackpearl) and database server sit on the same physical (or virtual) machine. The user logs into the application, the application delegates the users’s credentials to the K2 Server, which in turn delegates the credentials to SQL server. This is more commonly known as a single hop situation, illustrated below.
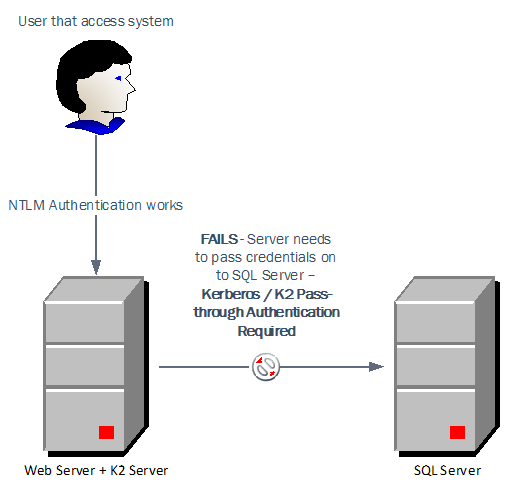
When we start scaling K2 out, we however often configure the K2 server and SQL Server to be hosted on separate machines..Within these solutions there is the requirement to impersonate a user from the K2 Server to the SQL servers, also commonly known as a double hop (See below diagram). The default NTLM authentication protocol as stated above does not provide the impersonation functionality required to support these solutions, and we need to revert to alternative means of Authentication.
One option for authentication is to make use of K2 Pass-Through Authentication, which is discussed here: http://help.k2.com/onlinehelp/k2blackpearl/icg/4.6.4/webframe.html#K2PA_-_Introduction.html.
Another option is to make use of the Kerberos security protocol which does provide the impersonation/delegation functionality needed to support such solutions.
- Setting up Kerberos for authentication
To set up Kerberos for authentication the following requirements need to be met:
- The SQL Server Service Account, as well as the IIS service accounts and K2 Blackpearl service accounts need to share a domain.
- Service principal names (SPNs) need to be setup for all the above mentioned service accounts
- Delegation needs to be enabled.
- Setting up the required SPN’s
For Kerberos authentication to work the following SPNS need to be setup:
SQL SERVER:
setspn -s MSSqlSvc/HOSTNAME:PORTNUMBER DOMAINSQLSERVICEACCOUNT
setspn -s MSSqlSvc/FQDN:PORTNUMBER DOMAINSQLSERVICEACCOUNT
K2 SERVER:
setspn -s K2Server/HOSTNAME:5252 DOMAINK2SERVICEACCOUNT
setspn -s K2Server/FQDN:5252 DOMAINK2SERVICEACCOUNT
setspn -s K2HostServer/HOSTNAME:5555 DOMAINK2SERVICEACCOUNT
setspn -s K2HostServer/FQDN:5555 DOMAINK2SERVICEACCOUNT
IIS:
And the following spns need to be setup for all of the different application pool accounts under which the different K2 modules is hosted:
setspn -s HTTP/HOSTNAME DOMAINIISSERVICEACCOUNT
setspn -s HTTP/FQDN DOMAINIISSERVICEACCOUNT
More information on SPNs can be found at https://msdn.microsoft.com/en-us/library/ms677949%28v=vs.85%29.aspx?f=255&MSPPError=-2147217396.
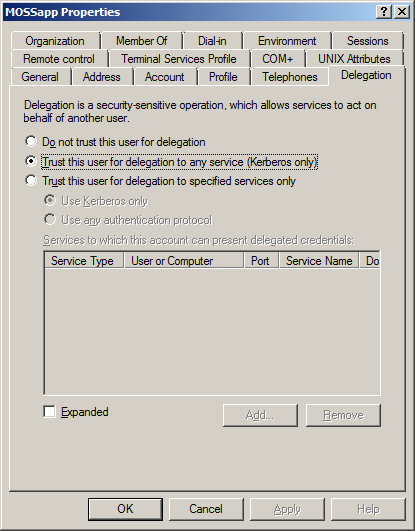
- Enabling delegation
The final step is to enable delegation on the service accounts.
More information on delegation can be found at: https://technet.microsoft.com/en-us/library/cc756906(v=ws.10).aspx
About Velocity IT
Velocity IT is a K2 partner that specialises in the design and development of K2 workflow, K2 SmartForms and K2 BPM solutions. Click here for more information…
Kerberos authentication for K2